Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher
Related Articles: Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher
- 2 Introduction
- 3 Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher
- 3.1 Historical Roots: A Journey Through Time
- 3.2 The Five-Letter Shift: A Unique Twist
- 3.3 Applications and Significance: Beyond Simple Encryption
- 3.4 FAQs: Addressing Common Questions
- 3.5 Tips for Using the Five-Letter Shift Cipher
- 3.6 Conclusion: A Glimpse into the World of Cryptography
- 4 Closure
Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher

The world of cryptography, the art of secure communication, is a fascinating realm of codes, ciphers, and hidden messages. While complex algorithms and intricate mathematical systems often dominate modern cryptography, a surprisingly simple method, the shift cipher, offers a glimpse into the fundamental principles of encoding and decoding information. One specific variation, the shift cipher with a five-letter shift, presents a unique and intriguing approach to encrypting text.
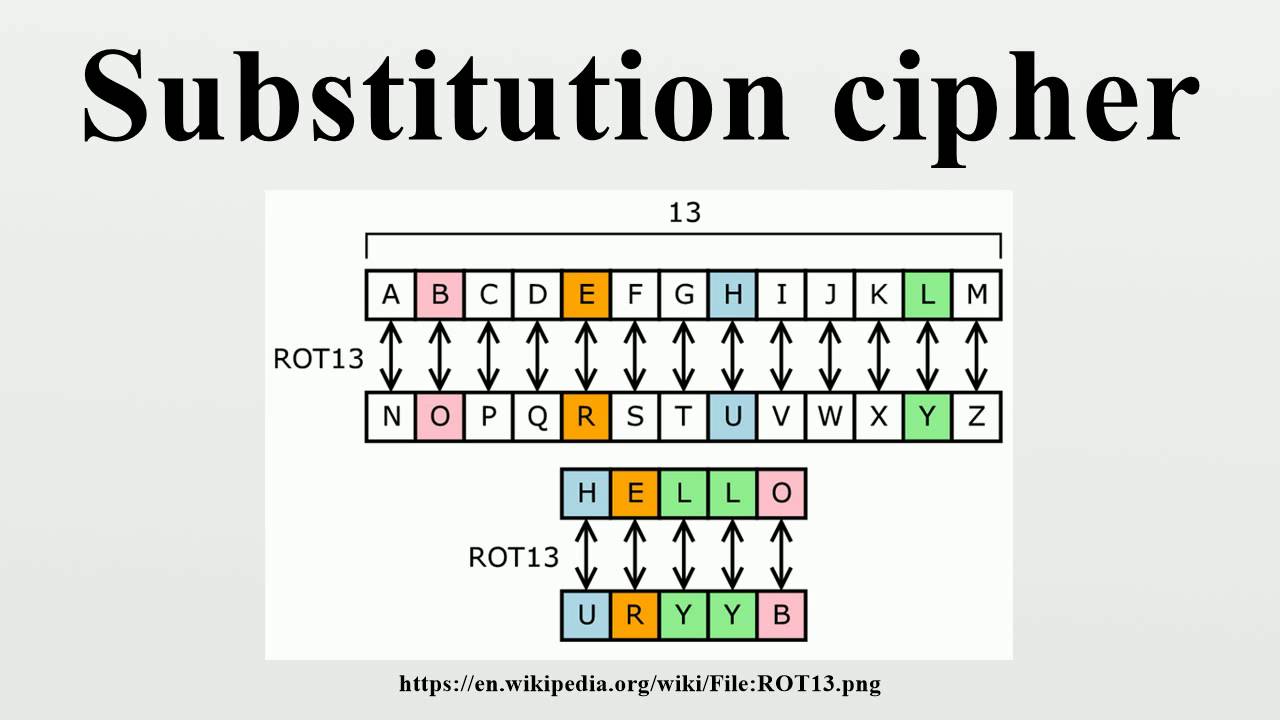
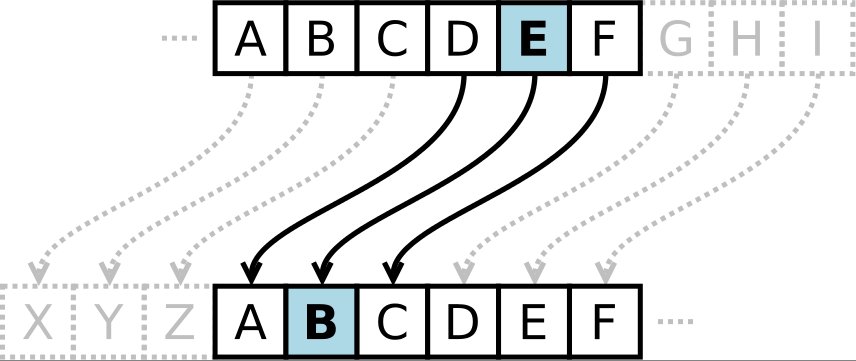
This method, often referred to as a Caesar cipher with a five-letter shift, relies on a straightforward principle: shifting each letter in a message five positions down the alphabet. For example, ‘A’ becomes ‘F’, ‘B’ becomes ‘G’, ‘C’ becomes ‘H’, and so on. This seemingly rudimentary approach, however, holds a surprising amount of historical significance and demonstrates the core concepts of cryptography in a readily accessible manner.
Historical Roots: A Journey Through Time
The shift cipher, in its various forms, has a rich history spanning centuries. Its origins can be traced back to ancient Roman times, where Julius Caesar, the renowned military leader and statesman, employed a similar cipher to protect his military communications. This method, later known as the Caesar cipher, involved shifting each letter three positions down the alphabet. While the exact details of Caesar’s cipher remain shrouded in historical debate, its basic principle – substituting letters with their shifted counterparts – has become a cornerstone of basic cryptography.
The Caesar cipher, with its simplicity and ease of implementation, gained widespread use throughout history. It found application in various contexts, from secret messages exchanged during wartime to personal correspondence seeking privacy. However, its simplicity also made it susceptible to cryptanalysis, the art of breaking codes. With the development of frequency analysis, a technique that analyzes the frequency of letters in a ciphertext, the Caesar cipher’s security became increasingly compromised.
The Five-Letter Shift: A Unique Twist
The five-letter shift cipher, a variation of the Caesar cipher, presents a unique approach to encryption. By shifting letters five positions down the alphabet, this method creates a distinct pattern that sets it apart from the more common three-letter shift. While still relatively straightforward, the five-letter shift offers a greater degree of complexity, making it more challenging to decipher without prior knowledge of the key.
For instance, the word "HELLO" would be encoded as "MJQQT" using the five-letter shift. This seemingly simple transformation creates a seemingly unintelligible message, effectively concealing the original text from unauthorized access. The five-letter shift, therefore, presents a rudimentary yet effective way to protect sensitive information.
Applications and Significance: Beyond Simple Encryption
While the five-letter shift might seem like a trivial tool in the modern age of sophisticated encryption algorithms, its significance extends beyond basic code-breaking. This simple cipher serves as a valuable educational tool, introducing fundamental concepts of cryptography in an engaging and accessible manner. By understanding the principles of letter substitution and shift encoding, individuals can gain a foundational understanding of the core ideas that underpin modern cryptography.
Furthermore, the five-letter shift can be incorporated into more complex cryptographic systems. It can be used as a building block for more sophisticated ciphers, where multiple layers of encryption are applied to enhance security. By understanding the workings of the five-letter shift, individuals can better appreciate the intricacies of modern cryptography and the challenges involved in securing sensitive information.
FAQs: Addressing Common Questions
Q: How does the five-letter shift cipher work?
A: The five-letter shift cipher involves shifting each letter in a message five positions down the alphabet. For example, ‘A’ becomes ‘F’, ‘B’ becomes ‘G’, ‘C’ becomes ‘H’, and so on. The process wraps around the alphabet, so ‘X’ becomes ‘C’, ‘Y’ becomes ‘D’, and ‘Z’ becomes ‘E’.
Q: Is the five-letter shift cipher secure?
A: The five-letter shift cipher is considered relatively insecure, especially compared to modern encryption methods. Frequency analysis can be used to easily break the cipher. However, it can serve as an educational tool for understanding basic cryptographic principles.
Q: What are the limitations of the five-letter shift cipher?
A: The main limitation of the five-letter shift cipher is its simplicity. It is easily susceptible to cryptanalysis, especially with frequency analysis. Additionally, the shift pattern is readily identifiable, making it vulnerable to attacks.
Q: What are some applications of the five-letter shift cipher?
A: The five-letter shift cipher can be used as an educational tool to introduce basic concepts of cryptography. It can also be incorporated as a building block in more complex ciphers.
Tips for Using the Five-Letter Shift Cipher
- Keep it simple: The five-letter shift cipher is best suited for short messages or for educational purposes.
- Avoid repetition: Repeating letters or patterns can make the ciphertext more susceptible to cryptanalysis.
- Use a key phrase: To enhance security, a key phrase can be used to create a more complex shift pattern.
- Combine with other methods: The five-letter shift can be combined with other encryption methods to create a more secure system.
- Understand its limitations: The five-letter shift cipher is not suitable for protecting highly sensitive information.
Conclusion: A Glimpse into the World of Cryptography
The five-letter shift cipher, while seemingly simple, offers a valuable glimpse into the world of cryptography. It demonstrates the fundamental principles of letter substitution and shift encoding, providing a foundational understanding of the core ideas that underpin modern encryption methods. While its security is limited, its simplicity and ease of implementation make it a valuable educational tool, enabling individuals to explore the fascinating realm of code-breaking and secure communication. As we navigate the increasingly digital world, understanding the basics of cryptography, even through seemingly simple methods like the five-letter shift, becomes increasingly crucial.






Closure
Thus, we hope this article has provided valuable insights into Unveiling the Secrets of a Simple Shift: Exploring the Power of a Five-Letter Cipher. We appreciate your attention to our article. See you in our next article!