Shifting Letters: A Fundamental Concept in Cryptography and Coding
Related Articles: Shifting Letters: A Fundamental Concept in Cryptography and Coding
Introduction
With great pleasure, we will explore the intriguing topic related to Shifting Letters: A Fundamental Concept in Cryptography and Coding. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Shifting Letters: A Fundamental Concept in Cryptography and Coding
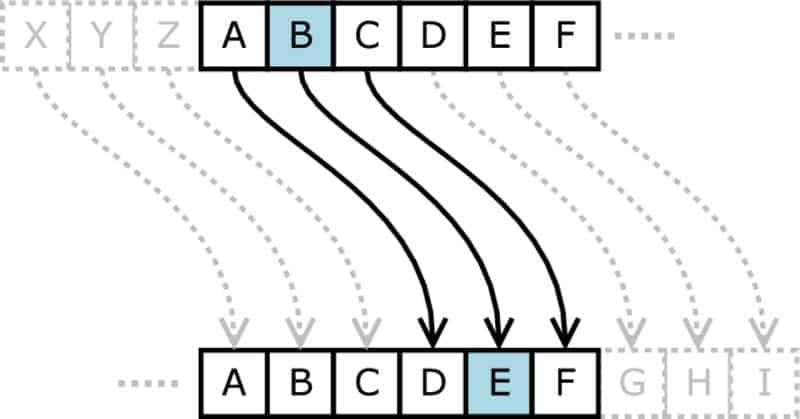
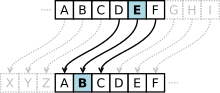
The seemingly simple act of shifting letters by one position within the alphabet, known as a "Caesar cipher" or a "shift cipher," holds a surprising significance in the world of cryptography and coding. This basic technique, while easily deciphered by modern standards, serves as a foundational building block for understanding more complex encryption methods and offers a valuable insight into the evolution of secure communication.
The Mechanics of Shifting Letters
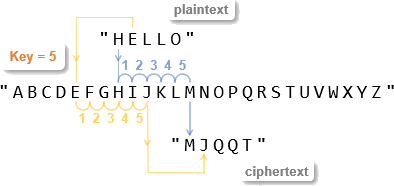
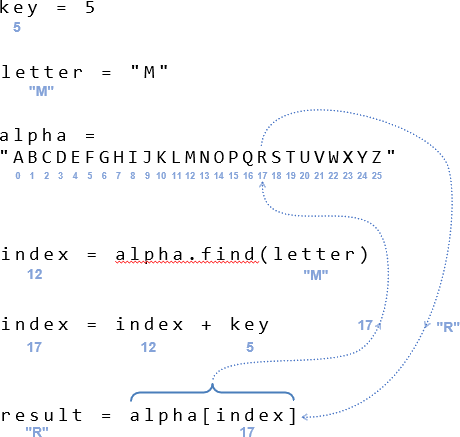
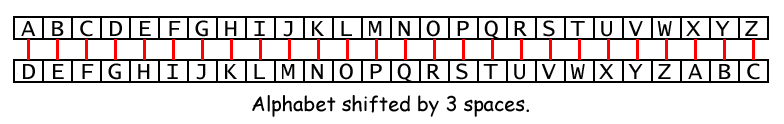
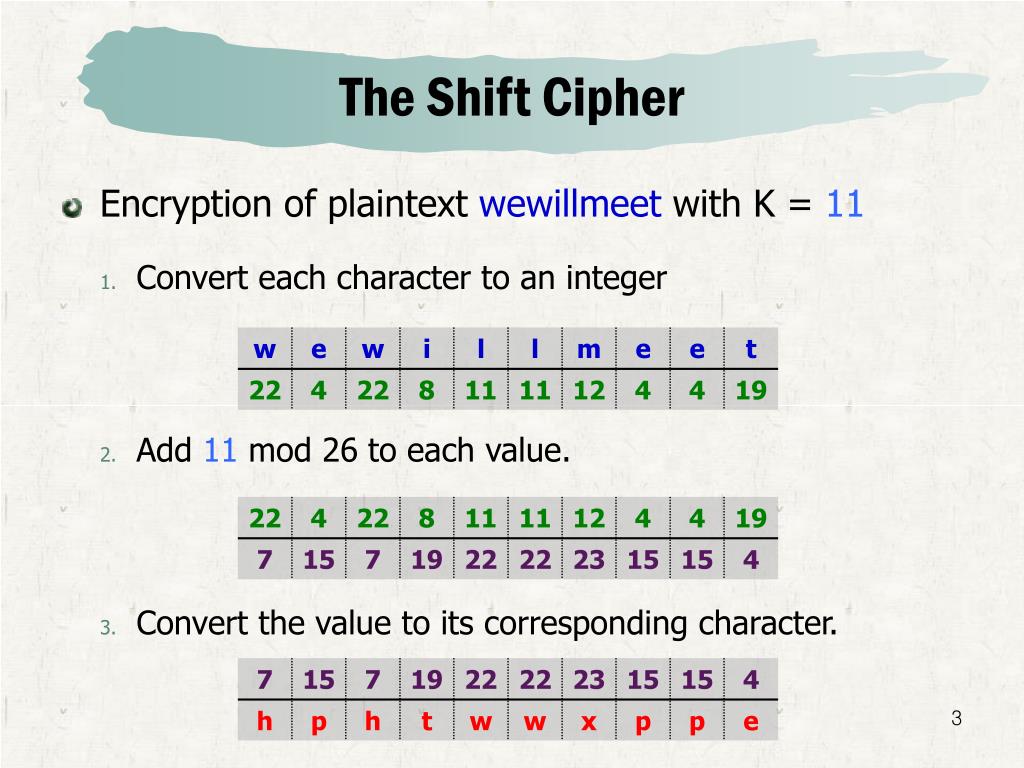
The core principle of shifting letters by one is straightforward. Each letter in a message is replaced by the letter that follows it in the alphabet, with "Z" wrapping around to "A." For example, "A" becomes "B," "B" becomes "C," and so on, until "Z" becomes "A." This transformation, while simple, effectively obscures the original message, rendering it unintelligible to anyone unfamiliar with the shifting method.
Historical Significance and Early Applications
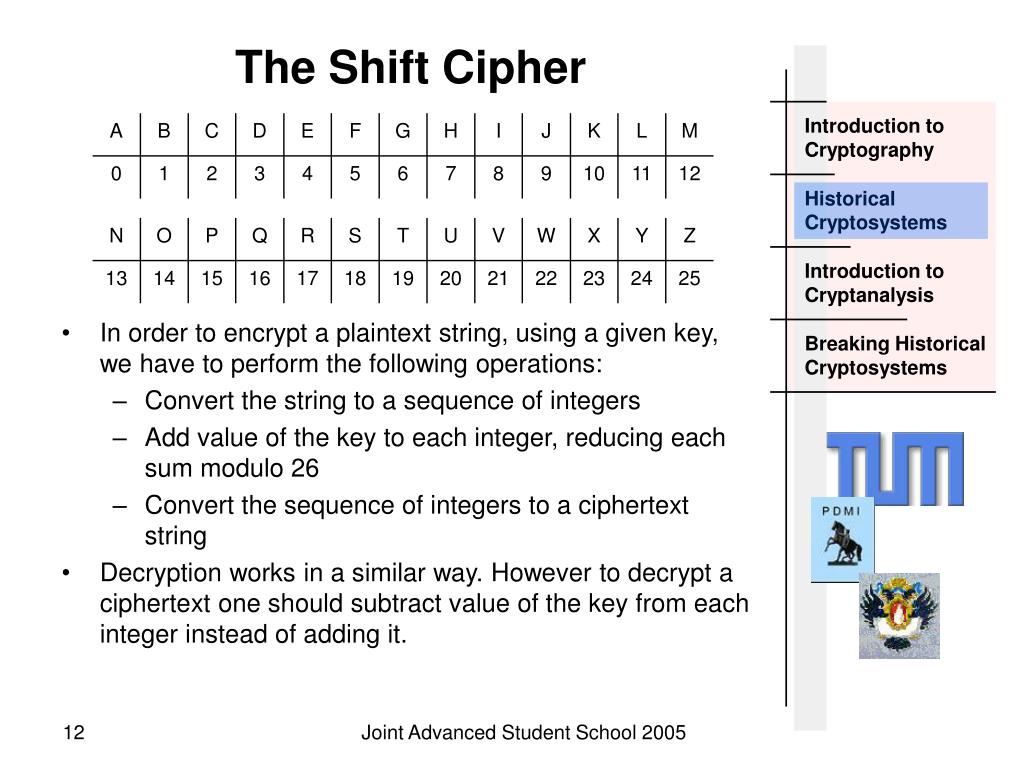
The Caesar cipher, named after the Roman emperor Julius Caesar who famously employed it for military communication, represents one of the earliest documented forms of cryptography. Its simplicity allowed for quick and efficient encryption, crucial for conveying sensitive information in a time when secure communication was paramount. The cipher’s historical significance lies not only in its early use but also in its influence on the development of more sophisticated encryption techniques.
Modern Relevance and Applications
While the Caesar cipher may seem outdated in the age of modern encryption algorithms, its underlying principles remain relevant. The concept of shifting letters, albeit in more complex forms, is still employed in various modern applications, including:
- Basic Encryption: Shifting letters by one can serve as a rudimentary encryption method for personal messages, particularly in situations where high-level security is not required.
- Educational Tool: The Caesar cipher provides a valuable educational tool for introducing students to the fundamental concepts of cryptography, demonstrating the principles of substitution and encoding.
- Code Breaking: Understanding the Caesar cipher helps in deciphering simple codes and serves as a stepping stone for learning more advanced code-breaking techniques.
Understanding the Limitations
Despite its historical significance and educational value, the Caesar cipher suffers from significant limitations:
- Easy Decipherment: The simplicity of the algorithm makes it easily breakable using frequency analysis, where the frequency of occurrence of each letter in the encrypted message can be compared to the frequency of letters in the standard language, revealing the shift pattern.
- Limited Security: The fixed shift value makes the cipher vulnerable to brute-force attacks, where all possible shift values are tested until the correct one is found.
- Susceptibility to Pattern Recognition: The consistent shift pattern creates predictable patterns in the encrypted message, making it susceptible to pattern recognition by experienced code breakers.
Beyond the Simple Shift: Variations and Enhancements
To address the limitations of the basic Caesar cipher, various enhancements and variations have been developed, including:
- Multiple Shifts: Instead of a fixed shift of one, multiple shift values can be used, making the cipher more complex and harder to decipher.
- Polyalphabetic Substitution: This technique employs multiple alphabets, each with a different shift value, further increasing the complexity of the cipher.
- Keyword-Based Shifts: Using a keyword to determine the shift value for each letter adds another layer of complexity, making the cipher more resistant to brute-force attacks.
These enhancements demonstrate the evolution of cryptography, highlighting the constant struggle between developing more secure encryption methods and finding ways to break them.
FAQs
Q: What is the difference between a Caesar cipher and a shift cipher?
A: The terms "Caesar cipher" and "shift cipher" are often used interchangeably. However, strictly speaking, a Caesar cipher refers specifically to a shift of three positions, while a shift cipher encompasses any shift value.
Q: Can the Caesar cipher be used for modern communication?
A: While the Caesar cipher can be used for basic encryption, it is not secure enough for modern communication. Its simplicity makes it easily breakable, rendering it unsuitable for protecting sensitive information.
Q: What are some examples of more advanced encryption methods?
A: Modern encryption methods include AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and ECC (Elliptic Curve Cryptography), which employ complex mathematical algorithms to provide much higher levels of security.
Tips for Understanding and Applying Shifting Letters
- Start with the basics: Understanding the Caesar cipher provides a solid foundation for exploring more advanced cryptography concepts.
- Practice code breaking: Attempting to decipher simple codes using frequency analysis and pattern recognition helps develop critical thinking skills and an understanding of code-breaking techniques.
- Explore variations: Experiment with different shift values and keywords to observe how they affect the complexity and security of the cipher.
- Learn about modern encryption methods: Understanding the limitations of the Caesar cipher highlights the need for more secure encryption methods and encourages further exploration of modern cryptography.
Conclusion
The simple act of shifting letters by one, while seemingly insignificant, holds a profound significance in the history and development of cryptography. It serves as a foundational concept, demonstrating the core principles of substitution and encoding, and provides a valuable educational tool for understanding the evolution of secure communication. While the Caesar cipher itself may be outdated, its underlying principles continue to inspire the development of more robust and complex encryption methods, shaping the future of secure communication in an increasingly digital world.


Closure
Thus, we hope this article has provided valuable insights into Shifting Letters: A Fundamental Concept in Cryptography and Coding. We thank you for taking the time to read this article. See you in our next article!